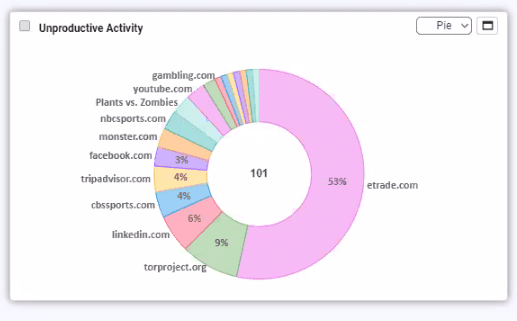
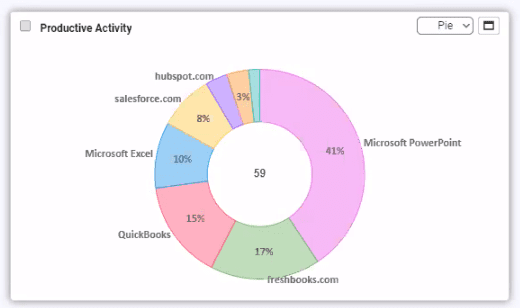
Work from Home Security–Is Your VPN Letting the Hackers In?

In the haste of the rapid changes coming down from government agencies, everyone who could work from home spent the last week or two getting their remote functionality set up.
While this was necessary, the last thing most people were thinking about was the potential security implications. Even though security may have been a thought, while quickly trying to think about how to handle everything else, it more than likely did not get the full attention it requires.
Now that we are past the initial shock and starting to work full-time from home, we wanted to put together some security posts to help organizations better secure their networks in this new environment. In these unusual circumstances, hackers always try to take advantage.
First, let’s talk about VPNs. They are incredibly useful tools if secured properly. Unfortunately, there have already been news stories about hackers targeting VPNs. What are they targeting? The answer is improperly configured and unpatched VPNs.
With that in mind, do you maintain and keep your firewalls up-to-date? The first step if you aren’t sure is to determine if your firewall and/or VPN appliances are up-to-date on firmware. Your IT engineers should be patching the hardware on at least a monthly basis, and sometimes even sooner if a critical update is available.
The next question to consider is whether you have configured the VPN properly. There are a few different ways to configure traffic on a client-to-site VPN. One option is to configure split tunneling, which is a way to only send network traffic specifically destined for the work network through the VPN. The other option is the opposite: all traffic goes through the VPN.
On the surface, split-tunneling sounds like the way to go. You do not want your employees personal web surfing to go through your network. What if they are streaming music while working? That seems like a bandwidth nightmare, right?
The problem with split-tunneling is that your employee’s computer becomes a gateway into your network. The employee could accidentally browse a malicious site via their home network which does not have any web filtering, causing that computer to become infected. Since the computer is connected to the VPN, that malware can enable hackers to access your business network by allowing them to enter through the employee’s home internet.
What about the problem of bandwidth? With the alternative, it is true you will use more bandwidth, but you have control over that bandwidth and, more importantly, the traffic. If you are concerned about music and video streaming, you can block that traffic from the VPN. After all, your employees are working from home. They could turn on the TV or radio.
You can also turn on web filtering, antivirus scans, intrusion detection and other firewall services to scan all traffic.
This way, the VPN will force all traffic to go through it. Any other devices on the home network will not be able to communicate with the laptop – the Xbox, Alexa, Google devices, etc. It will be in a quarantine of sorts. This dramatically improves security and will limit the exposure of your internal business network.
Finally, you should limit the type of traffic that can go through the VPN. If most of the traffic is just web traffic, only allow web traffic. If it’s a database application on your network, you can limit traffic to that database. List everything users need to access and implement access control policies to allow only that traffic.
As always, if you have questions about VPNs or are unsure about your security, reach out to us without hesitation. We are here to help.
Stay tuned for more security information to keep your business secure while your employees are working from home.